Revolutionising Cross-Chain Security: The Dual-Layer Breakthrough
Existing cross-chain communication protocols have historically been trapped between two imperfect approaches.
- Pure cryptographic methods offer rigorous verification but suffer from prohibitive computational costs.
- Conversely, economic security models rely on financial incentives but remain vulnerable to centralisation risks and potential coordinated attacks.
Concero V2 introduces an innovative hybrid framework that go beyond these limitations by inventive combining cryptographic verification and economic accountability.
This dual-layer approach creates a self-reinforcing security ecosystem where technological and economic mechanisms work in perfect synchronisation.
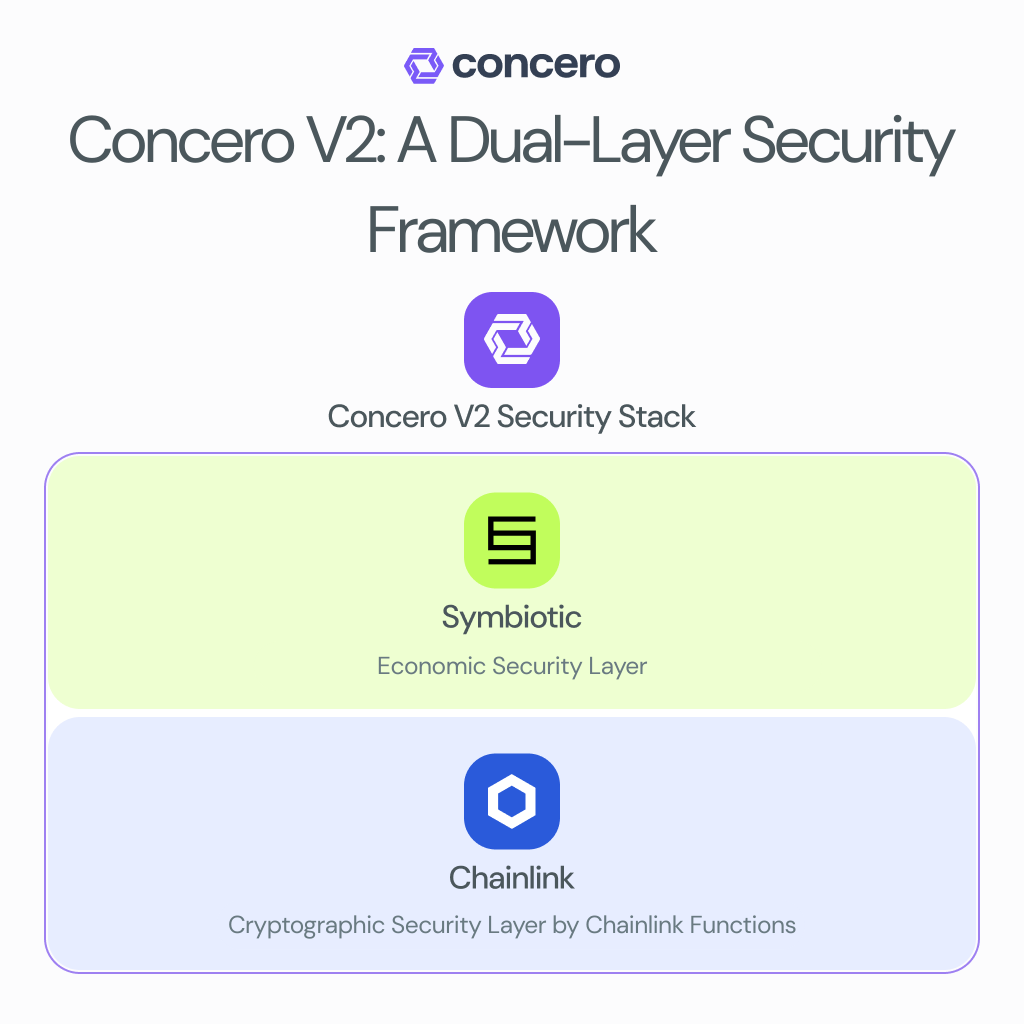
Cryptographic Layer: The Chainlink Functions Advantage
At the core of the first security layer lies Chainlink Functions, a decentralised compute network that generates robust and tamper-proof cryptographic proofs. Unlike traditional single-point verification methods, this layer leverages a Decentralised Oracle Network (DON) consisting of four independent nodes. Each node independently validates transaction data, ensuring that consensus can only be reached through rigorous, multi-node verification.
The verification process is meticulously designed. When a transaction is initiated, the system performs multiple security checks:
- Signature recovery to confirm node authenticity
- Consensus validation requiring at least three independent node contributions
- Hash verification to ensure data integrity during transmission
Economic Security Layer: Symbiotic's Innovative Restaking
The second layer, implemented through Symbiotic's restaking infrastructure, introduces an economic security paradigm that transforms potential vulnerabilities into strengths.
The protocol's slashing mechanism is particularly innovative. By requiring operators to stake significant economic collateral, Concero V2 creates a self-regulating ecosystem where operators are financially incentivised to maintain uptime, with slashing penalties applied only if they fail to post timely reports to the destination chain.
Moreover, the challenge period has been dramatically reduced from traditional week-long windows to a mere 10-20 seconds, enabling unprecedented capital efficiency.